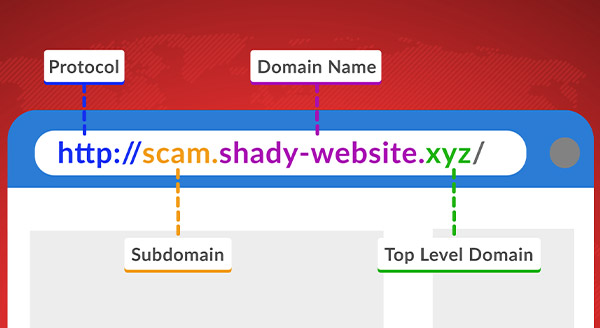
7 Unexpected Ways Hackers Can Access Your Accounts
The digital age has made our lives easier than ever, but it has also made it easier for hackers to take advantage of our online weaknesses. Hackers are getting smarter and using more creative ways to get into people’s personal and business accounts. It’s easy to think of weak passwords and [...]